5 minutes
Friendica CVE-2024-27728, CVE-2024-27729, CVE-2024-27730, CVE-2024-27731 Disclosure
This a short post disclosing the details of four vulnerabilities affecting Friendica 2023.12 which I identified in February 2024. The following vulnerabilties were discovered:
- CVE-2024-27729:
Stored Cross Site Scripting (XSS) in calendar event feature. - CVE-2024-27730:
Access control, insecure direct object reference (IDOR) issue in calendar event feature. - CVE-2024-27728:
Reflected XSS in Babel debug feature. - CVE-2024-27731:
Reflected XSS via uploaded attachment file.
Each of the XSS vulnerabilities could be exploited to steal an administrator users session cookie or a regular users password hash. The permissions issue affecting the calendar event feature could be exploited to make calendar event posts on behalf of any other user on the Friendica server. When combined with the stored XSS affecting this feature this would allow an attacker to target any user on the server and steal their cookie or password hash when they sign in.
CVE-2024-27729 - Stored XSS in Calendar Event Posts
Friendica has a feature for creating events and sharing them with your followers. The events get shown in your followers feed as seen below:
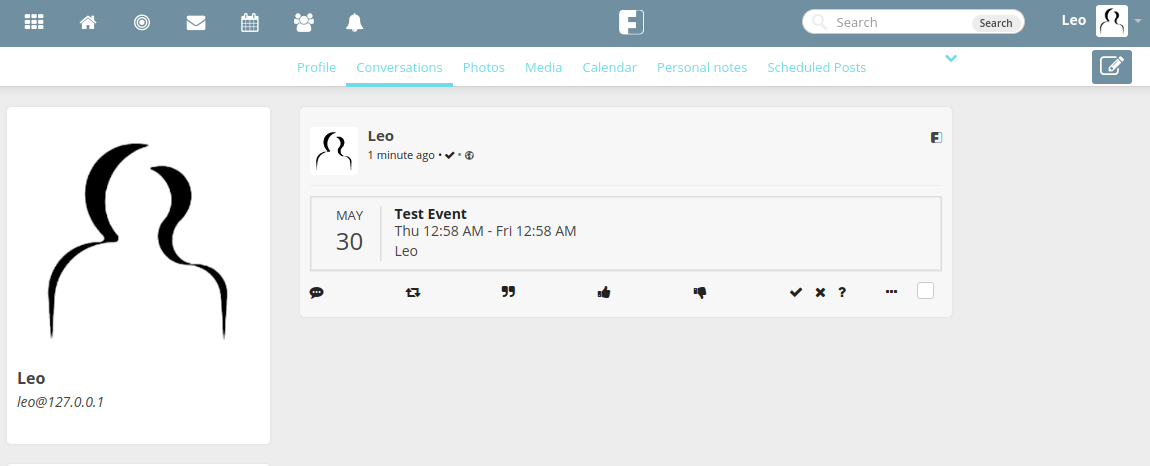
The text provided in the location parameter when creating the event was not being santised or escaped when it was displayed in users feeds. This meant a simple XSS payload could be embedded within this parameter as shown in the request below:
The javascript then executes in the browser of any user who views the event in their feed, i.e all of the users followers.
Exploiting the XSS with a CSRF Request
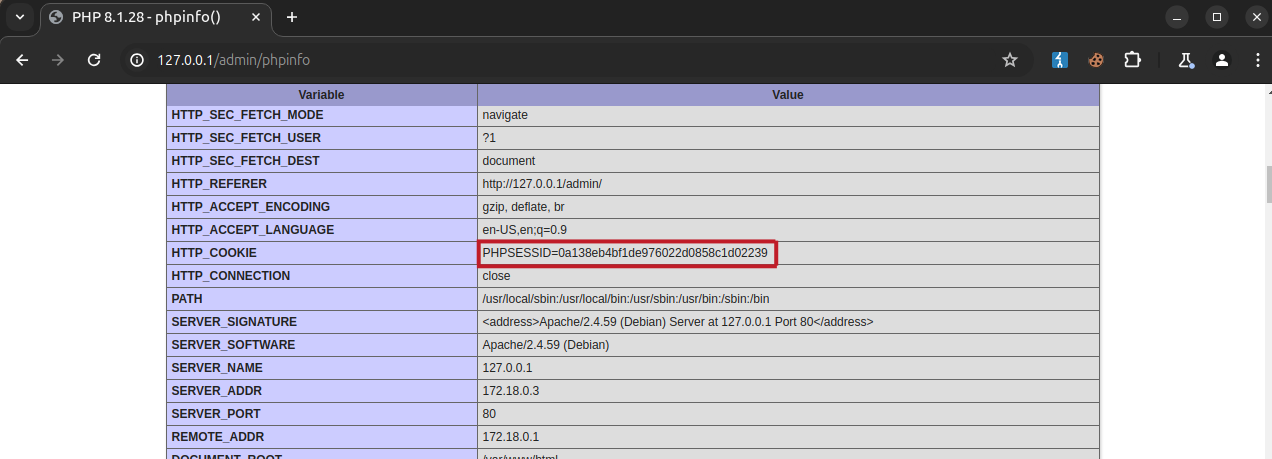
The primary session cookie for Friendica PHPSESSID was set with the HttpOnly flag meaning that it could not be accessed from JavaScript and therefore it was not possible to directly exfiltrate it from the context of the XSS. However, Friendica administrators had access to the phpinfo endpoint which disclosed the PHPSESSID cookie value.
There was also another endpoint that allowed users to backup their Friendica profile information which disclosed the logged in users password hash.
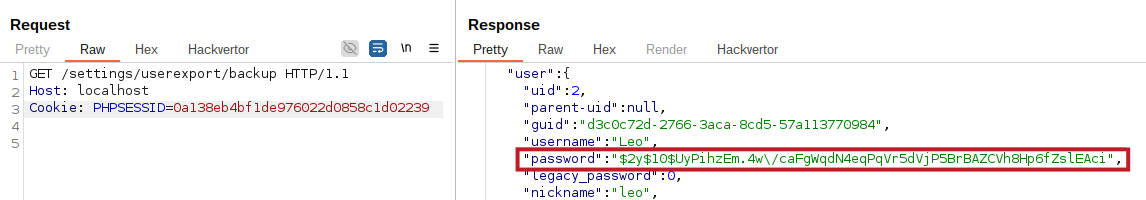
Using these two endpoints it was possible to create an XSS payload that would exfiltrate the users password hash and if the user was an admin also their session cookie:
This payload could then be URL encoded and then injected into the location parameter of a new event. When any user views the event in their feed, a request containing their secrets is sent to the attackers server.
CVE-2024-27730 - Calendar Event IDOR Access Control Issue
There was also an IDOR vulnerability in the calendar event feature that allowed calendar events to be created on behalf of other users. This significantly heightened the impact of the previously described XSS vulnerability because, instead of solely targeting your followers, it made it possible to target any users on the server.
To make a calendar event as another user the contact ID cid value could simply be changed to another users contact ID in the POST request when creating a new calendar event:
At this point the calendar event will be created as the other user, however, it is not shared with other users on the server. From looking at the source code the following lines of code are present at the end of the function which handles requests to create the events:
This shows that the event post will only be shared with other users when the cid value is 0. This clarifies why, when it is altered to another user’s contact ID, it is not displayed on that user’s or their followers' feeds.
To circumvent this the following POST request can be sent to edit the existing event:
When editing the event it retains its original author and since the cid value has been changed to 0 the event is sent to the feed of all of the target users followers.
CVE-2024-27728 - Babel Debug Endpoint Reflected XSS
The text parameter on the babel debug endpoint was vulnerable to reflected XSS as it was not escaped before being returned in the HTML reponse:
https://<FRIENDICA-SERVER>/babel?text=<script>alert()</script>&type=html
The XSS payload provided in the sections above could also be used here to steal the victims password hash or session cookie if they are tricked into browsing to the malicious link.
CVE-2024-27731 - Lack of Uploaded File Type Validation Leads to XSS
There was no validation on the type of files that could be uploaded to the media attachment endpoint. It was not possible to achieve RCE via uploading a PHP file to the endpoint because the contents of the file were being stored in the Friendica database rather than as a file on the server. However, it was possible to achieve XSS by uploading an HTML file containing JavaScript, which could then be sent as a link to a victim user.
The following POST request uploads the HTML file:
The uploaded file could then be linked to a victim with a link like the following, where <ATTACHMENT-ID> is the ID of the attachment returned in the previous POST request:
https://<FRIENDICA-SERVER>/attach/<ATTACHMENT-ID>?attachment=0
Note, the attachment parameter must be set to 0 so that the Content-Disposition: attachment header does not get added and cause the file to be downloaded as an attachment.