6 minutes
OffSec Proving Grounds: ClamAV - Walkthrough
This post contains rough notes explaining my process for exploiting the ClamAV Proving Grounds box while preparing for the OSCP certification.
My Process
This is a walkthrough for the Offsec Proving Grounds Practise box titled ClamAV.
Firstly I checked what ports were open on the machine by running a port scan with nmap:
I also scanned UDP ports but only the top 2000 since scanning UDP is slow:
A webserver was running on port 80 so I browsed to the website and saw that there was some binary data there:
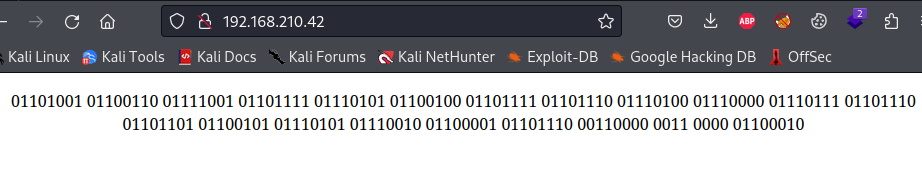
Once converted to ascii that resulted in the following string: “ifyoudontpwnmeuran00b”
So just some motiviation for us…
The SNMP UDP port was open so that was the next thing I decided to enumerate. First I tested the community string “public” and that seemed to work so I used snmpbulkwalk to enumerate all of the MIBS and save them to a file:
After manually scanning the output I found a few pieces of useful information:
- Information about the system:
SNMPv2-MIB::sysDescr.0 = STRING: Linux 0xbabe.local 2.6.8-4-386 #1 Wed Feb 20 06:15:54 UTC 2008 i686 - ClamAV is installed which is no surprise given the labs name:
HOST-RESOURCES-MIB::hrSWRunPath.3782 = STRING: “/usr/local/sbin/clamd”
HOST-RESOURCES-MIB::hrSWRunPath.3784 = STRING: “/usr/local/sbin/clamav-milter” - The arguments that ClamAV is running with:
HOST-RESOURCES-MIB::hrSWRunParameters.3784 = STRING: “–black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl”
At this stage I did a bit of research on what the black hole mode is by googling it. While searching I noticed that there was a RCE vulnerability in the black hole mode for clamav milter: CVE-2007-4560
Since the box has clamav-milter installed and is running SNMP this looked promising.
I found the following exploit written in go:
https://gist.github.com/0xjbb/fdf1678addf0c957bf2b284b29e4dff4
First I tested if the RCE exploit worked by trying to execute a ping command on the victim to send a few ping packets to my own machine.
I began monitoring on the tun0 interface for icmp (ping) packets:
And then ran the exploit with the ping command:
I received the ping packets on kali, showing that the RCE was successful:
Now that I knew the machine was vulnerable I used the scripts -b option which executes a bind shell:
Then I connected to the bind shell with netcat, where I got a shell as the root user so no privilege escalation was necessary: